Introduction
In today’s digital world, the concepts of privacy and security are increasingly interdependent, yet often in tension with one another. As individuals, businesses, and governments rely more heavily on digital platforms, the amount of data generated is unprecedented. While this data has the potential to improve lives and enhance services, it also raises significant concerns about privacy, security, and how to protect sensitive information.
Privacy refers to an individual’s right to control their personal data and the freedom from unauthorized surveillance or intrusion. Security, on the other hand, refers to the protection of data and systems from cyber threats, attacks, and unauthorized access. The challenge lies in balancing these two principles. Too much emphasis on security can infringe upon privacy, while too much focus on privacy can leave systems vulnerable to malicious attacks.
This article explores the critical need to strike a balance between privacy and security, examining the technological, legal, and ethical considerations involved. We will analyze the current landscape of data privacy and cybersecurity, the risks and challenges, and the solutions and strategies that can help find a middle ground. The article also looks at the evolving role of governments, organizations, and individuals in navigating this delicate balance.
The Importance of Privacy and Security
Before diving into the challenges of balancing privacy and security, it’s important to understand why both are essential:
1. The Importance of Privacy
Privacy is a fundamental human right, recognized in international law and enshrined in various constitutions and human rights frameworks. In the digital age, privacy protection is becoming more critical as personal data is continuously collected by companies, governments, and third parties. A violation of privacy can lead to:
- Identity Theft: Unauthorized access to personal information, such as social security numbers or credit card details, can result in financial loss and reputational damage.
- Surveillance: Excessive surveillance, whether by governments or private corporations, can result in the erosion of civil liberties and freedom of expression.
- Loss of Autonomy: The control over personal data and its use can impact individuals’ sense of control over their lives, leading to a lack of trust in institutions and a chilling effect on free speech.
Privacy gives individuals the ability to control what information they share and with whom, which is vital for maintaining personal autonomy and dignity. The increasing use of personal data, particularly by large corporations, has raised serious concerns about the extent to which privacy is respected and protected.
2. The Importance of Security
Cybersecurity is critical for safeguarding data from malicious actors, such as hackers, cybercriminals, and state-sponsored threats. Data breaches, cyberattacks, and ransomware attacks have become more frequent and sophisticated, threatening everything from individual bank accounts to national infrastructure.
Key aspects of security include:
- Data Integrity: Ensuring that data remains accurate and unaltered, preventing unauthorized modifications.
- Confidentiality: Protecting sensitive information from unauthorized access.
- Availability: Ensuring that data and services are available when needed and protected from disruptions caused by cyber threats.
Without adequate security measures, sensitive information such as medical records, financial transactions, and business operations could be compromised, leading to catastrophic financial, reputational, and operational damage.
The Conflict Between Privacy and Security
Despite their shared importance, privacy and security often conflict. To understand why, it’s essential to look at how the two concepts interact:
1. The Tradeoff Between Privacy and Security
- Surveillance and Monitoring: Security measures often involve monitoring communications, network traffic, or even individual behaviors. While this can improve security, it may also infringe on personal privacy. For example, surveillance technologies such as CCTV cameras or internet traffic monitoring can create a sense of security but may also lead to unwanted intrusion into people’s private lives.
- Data Collection and Analysis: In order to protect systems, security protocols often require the collection of vast amounts of data, including personal information. While this data can be used to identify threats and improve defenses, it also creates privacy risks. The more data collected, the greater the chance that it will be misused or fall into the wrong hands.
- Encryption and Access Control: Encryption is a vital tool for securing data. However, encryption also limits law enforcement’s ability to access data during investigations, leading to concerns that privacy-focused encryption methods may hinder the fight against cybercrime and terrorism.
2. The Erosion of Trust
When either privacy or security is compromised, trust can erode. For instance, if companies over-collect data under the guise of improving security, individuals may become wary of sharing information online. On the other hand, if security measures are too lax, it may lead to data breaches, resulting in a loss of consumer confidence.
This erosion of trust can have far-reaching consequences for businesses, as customers become more reluctant to share their data. It can also harm government institutions, as citizens become skeptical of surveillance programs and government access to private information.
3. The Zero-Sum Dilemma
The zero-sum dilemma in balancing privacy and security suggests that focusing too much on one will necessarily weaken the other. The more control we give governments and companies over our data for security reasons, the more privacy we lose. On the other hand, if we place too much emphasis on personal privacy, it may leave us vulnerable to cyberattacks and other security breaches.
The challenge, therefore, is to find a way to ensure that neither privacy nor security is unduly sacrificed for the sake of the other. Both are vital, and a delicate balance must be maintained.
Legal and Ethical Frameworks
To navigate the challenges of balancing privacy and security, several legal and ethical frameworks have emerged. These frameworks aim to guide governments, corporations, and individuals in managing the delicate relationship between privacy rights and security needs.
1. The General Data Protection Regulation (GDPR)
The General Data Protection Regulation (GDPR), enacted by the European Union in 2018, is one of the most comprehensive privacy laws in the world. It aims to protect individuals’ personal data and privacy while setting guidelines for how companies and organizations collect, store, and process data.
Under the GDPR, companies must seek explicit consent from individuals before collecting their data, inform users about how their data will be used, and allow individuals to request that their data be deleted or corrected. The regulation places stringent requirements on data security, mandating that companies take appropriate measures to protect personal data from breaches.
While GDPR is a strong privacy-focused regulation, it also acknowledges the importance of security by requiring organizations to implement robust security measures to prevent unauthorized access to personal data. This represents an attempt to strike a balance between privacy and security.
2. The USA PATRIOT Act and National Security
In contrast to the GDPR, the USA PATRIOT Act passed after the September 11 attacks, exemplifies the prioritization of security over privacy. The law grants government agencies broad powers to conduct surveillance and collect data to prevent terrorism. This has raised concerns about the loss of civil liberties, particularly regarding the mass collection of phone records, email communications, and other forms of personal data.
The tension between national security and privacy rights is a constant source of debate, especially in the context of digital surveillance and data collection. Proponents of national security argue that increased surveillance is essential for preventing threats, while privacy advocates contend that such measures infringe on individual freedoms and civil rights.
3. Ethical Considerations
The balance between privacy and security also raises ethical questions. For instance, how much surveillance is acceptable in the name of security? Should governments be allowed to access encrypted communications to prevent crimes, or does that violate fundamental privacy rights?
Ethical frameworks often call for the principle of proportionality, which suggests that security measures should be proportionate to the threat they are trying to mitigate. In other words, surveillance and data collection should be no more invasive than necessary to achieve security goals.
Similarly, the ethical principle of autonomy asserts that individuals should have control over their personal data and how it is used, meaning that privacy should be respected even when security concerns arise.
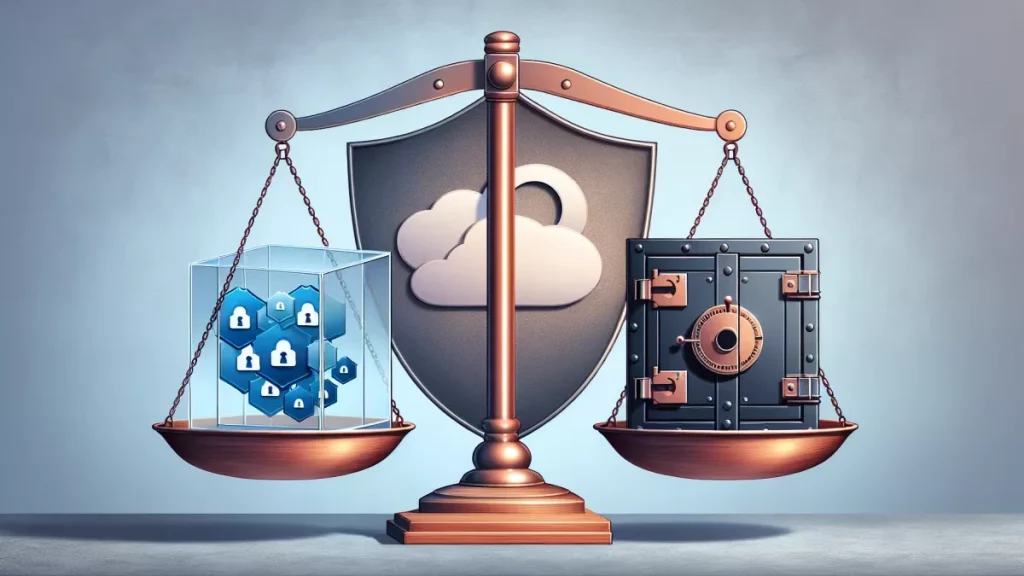
Technological Solutions for Balancing Privacy and Security
To mitigate the tension between privacy and security, a number of technological solutions are being developed and adopted. These solutions aim to provide the benefits of both privacy and security, without unnecessarily compromising either.
1. End-to-End Encryption
One of the most promising solutions for balancing privacy and security is end-to-end encryption. This method ensures that only the sender and recipient of a message can read its content, preventing third parties—including service providers and hackers—from accessing sensitive data.
While encryption improves privacy, it also enhances security by protecting data from unauthorized access. However, as mentioned earlier, encryption also poses challenges for law enforcement and security agencies, who may be unable to access encrypted data during investigations. Striking a balance between secure encryption and the ability to investigate cybercrimes remains a challenge.
2. Differential Privacy
Differential privacy is another innovative approach that allows data analysis while preserving individual privacy. This technique involves adding random noise to data sets so that individual data cannot be identified, yet the data can still be used for aggregate analysis. For example, businesses can use differential privacy to analyze user trends without exposing sensitive personal data.
Differential privacy allows organizations to gather insights and make data-driven decisions without compromising the privacy of individuals. It represents a key step toward reconciling the need for data analysis with the right to privacy.
3. Privacy-Enhancing Technologies (PETs)
Privacy-enhancing technologies (PETs) include tools like anonymization, tokenization, and secure multi-party computation that can safeguard personal data while allowing organizations to perform necessary functions. PETs aim to minimize the collection of personally identifiable information (PII) while still enabling organizations to process data for legitimate purposes.
These technologies are helping to bridge the gap between privacy and security, providing more granular control over personal data and ensuring that data is used responsibly and securely.
Conclusion
The balance between privacy and security is one of the most complex and important issues in the digital age. As data collection and surveillance become ubiquitous, the need for robust privacy protections is more critical than ever. At the same time, the increasing threat of cyberattacks and data breaches underscores the importance of strong security measures.
Finding a balance between these two concerns requires cooperation across multiple domains: technology, law, policy, and ethics. By leveraging technological innovations like encryption and differential privacy, adhering to robust legal frameworks like the GDPR, and applying ethical principles of autonomy and proportionality, we can achieve a more balanced and responsible approach to privacy and security.
As we move forward, the challenge will be to continue adapting to new technologies and emerging threats, ensuring that the delicate balance between privacy and security is maintained in a way that protects both individual rights and collective safety.